Applications related to the Internet of Things (IoT) are continuously growing, and one protocol is particularly popular, especially in the field of building management: the LoRaWAN protocol. Designed to provide low-power wireless connectivity, LoRaWAN technology enables communication between low-cost radio sensors with very low power consumption. Let’s discover together the key principles and advantages of the LoRaWAN protocol.

What is the LoRaWAN Protocol?
Based on LoRa technology, the LoRaWAN protocol is a radio communication protocol specifically designed to allow devices to transmit data over long distances while maintaining minimal power consumption. In other words, a LoRaWAN sensor can send data over very long distances with excellent levels of autonomy. Enless sensors are compatible with the LoRaWAN protocol.
2. Architectures of the LoRaWAN Protocol
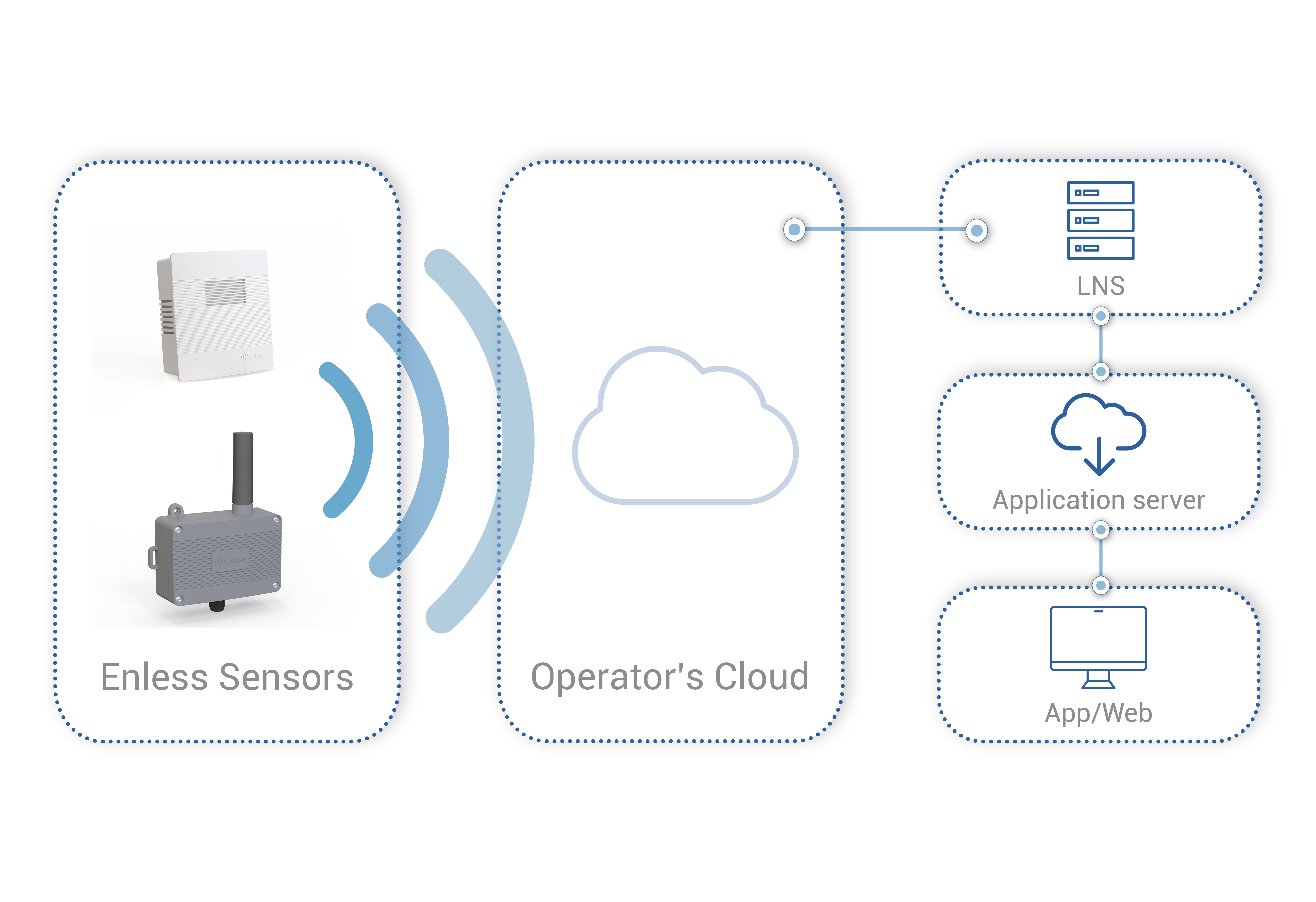
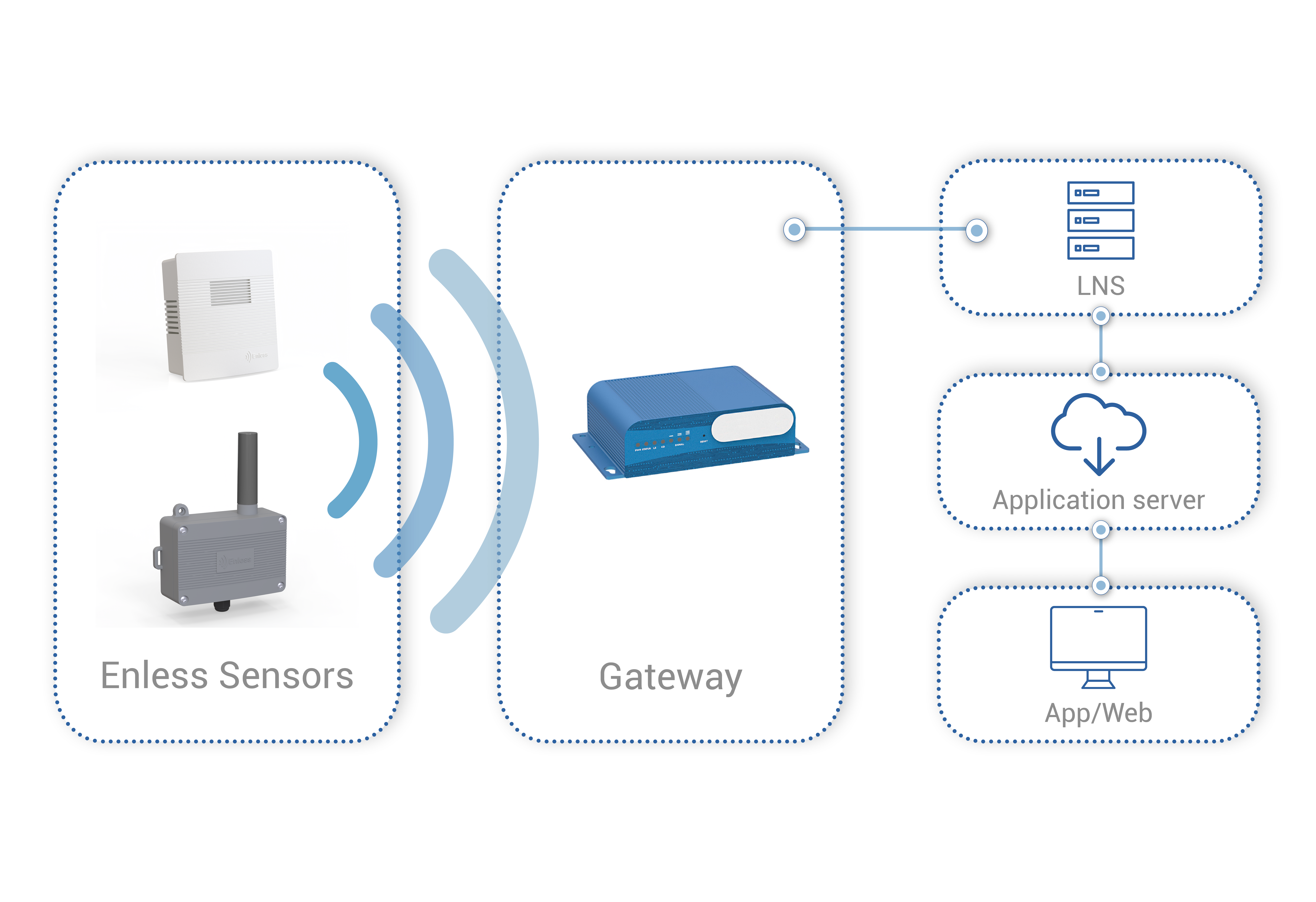
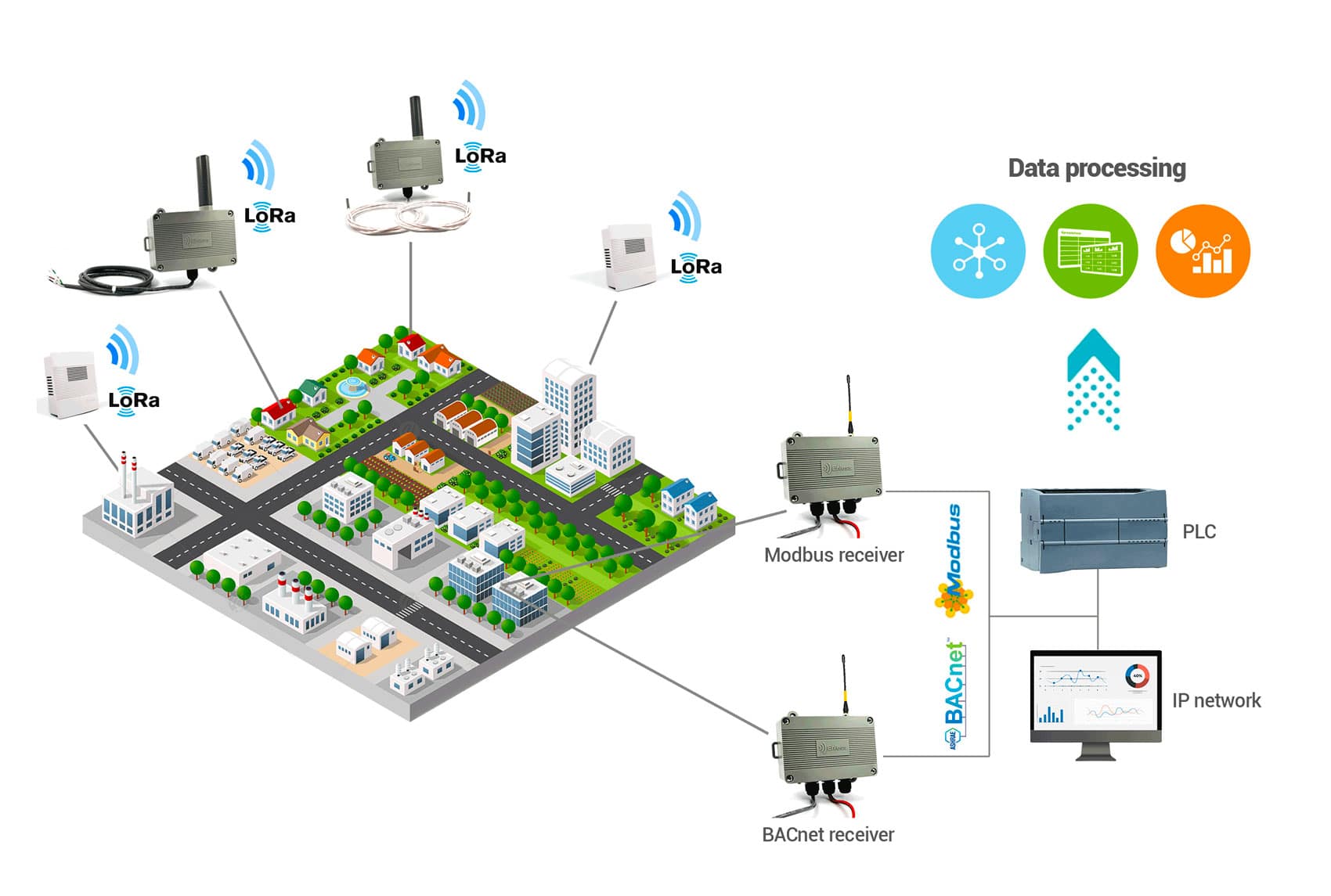
1. Sensors (or nodes)
Sensors collect data and transmit it to the gateways. Enless offers a complete range of LoRaWAN sensors.
2. Gateways
LoRaWAN gateways act as concentrators, receiving and transmitting data from LoRaWAN sensors to the Network Server.
3. The Network Server
The LoRa Network Server (LNS) processes the data and makes it available for IoT applications.
3. Advantages of the LoRaWAN Protocol
1. Extended Range
Thanks to modulation principles and the adaptation of Spreading Factors, LoRa technology allows communication over distances of several kilometers, making it the ideal protocol for applications requiring extensive coverage.
2. Low Power Consumption
LoRaWAN devices are designed to operate with minimal power consumption, extending the battery life of sensors.
3. Scalability
A LoRaWAN network can support thousands of sensors, making it perfectly suited for large-scale deployments.
4. Operating Modes
The LoRaWAN protocol offers three operating modes: Class A, Class B, and Class C. Each mode offers trade-offs between power consumption and network responsiveness.
More information on the Things Network (TTN) website
5. Security
Security is a major concern in IoT, and the LoRaWAN protocol integrates encryption mechanisms (AES128) to ensure information confidentiality and node authentication. During startup, the node automatically attempts to connect by sending a « join » request to the LoRaWAN server via the gateway. If the server accepts the request, two session keys, called NwkSKey and AppSKey, are generated from a « common secret ». This « common secret, » named AppKey, is stored both on the node (permanently in the code) and on the gateway. This process is known as « Over the Air Activation » (OTAA).